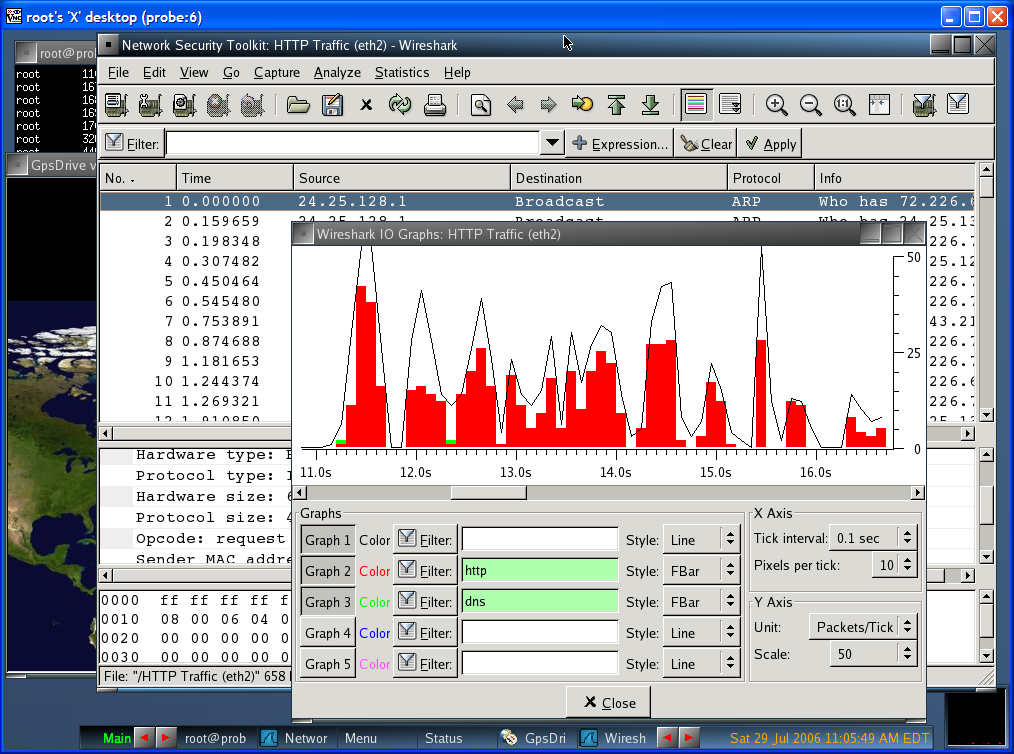
 The Network Security Toolkit (NST) is a ISO live CD/DVD (NST Live) based on Fedora. The toolkit was designed to provide easy access to best-of-breed Open Source Network Security Applications and should run on most x86/x86_64 platforms.
The Network Security Toolkit (NST) is a ISO live CD/DVD (NST Live) based on Fedora. The toolkit was designed to provide easy access to best-of-breed Open Source Network Security Applications and should run on most x86/x86_64 platforms.
The main intent of developing this toolkit was to provide the network security administrator with a comprehensive set of Open Source Network Security Tools. The majority of tools published in the article: Top 100 Security Tools by INSECURE.ORG are available in the toolkit.
Some of the tools available in this live are: Ntop, wireshark, nmap with the vizualization tool ZenMap and kismet.
Many tasks that can be performed within NST are available through a web interface called NST WUI. Among the tools that can be used through this interface are nmap with the vizualization tool ZenMap, ntop, a session manager for VNC, a minicom-based terminal server, serial port monitoring, and WPA PSK management.
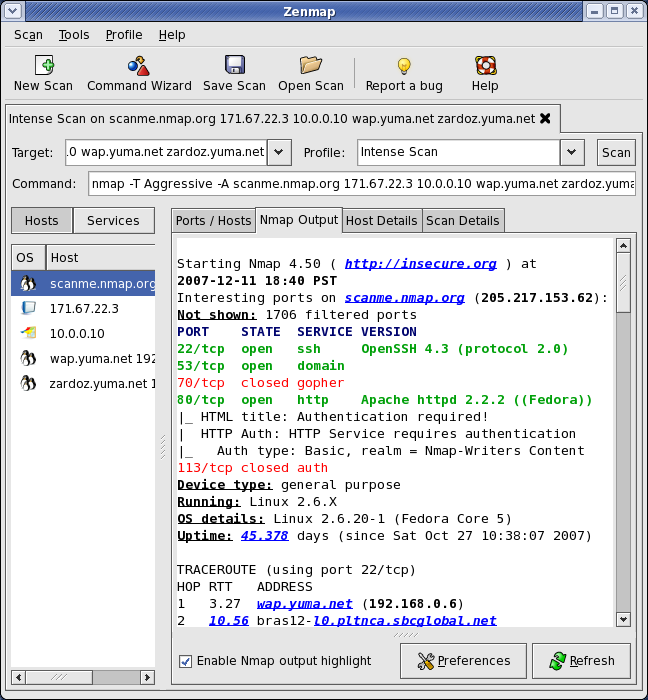
You can read some of my articles about Nmap and Ntop following the links, for Nmap you got also Zenmap.
Zenmap is the official Nmap Security Scanner GUI. It is a multi-platform free and open source application which aims to make Nmap easy for beginners to use while providing advanced features for experienced Nmap users. Frequently used scans can be saved as profiles to make them easy to run repeatedly. A command creator allows interactive creation of Nmap command lines. Scan results can be saved and viewed later. Saved scan results can be compared with one another to see how they differ. The results of recent scans are stored in a searchable database.
On NST are also available Nagios and Argus, 2 software that can be used for network monitoring, you can check the status of various services, like web server, pop/imap mails erver or other services that in general you can test directly with a network connection.
Another feature nice, and really “scenic” is that NST includes visualization of ntop, wireshark, traceroute and kismet data by geocoding the host addresses and displaying them via Google Earth.
For this NST use a custom tool: nstgeolocate — Geolocate hosts obtained from an ‘ntop’ session or Geolocate IPv4 Address conversations from a network packet capture file on a Mercator World Map projection or Global imagery. 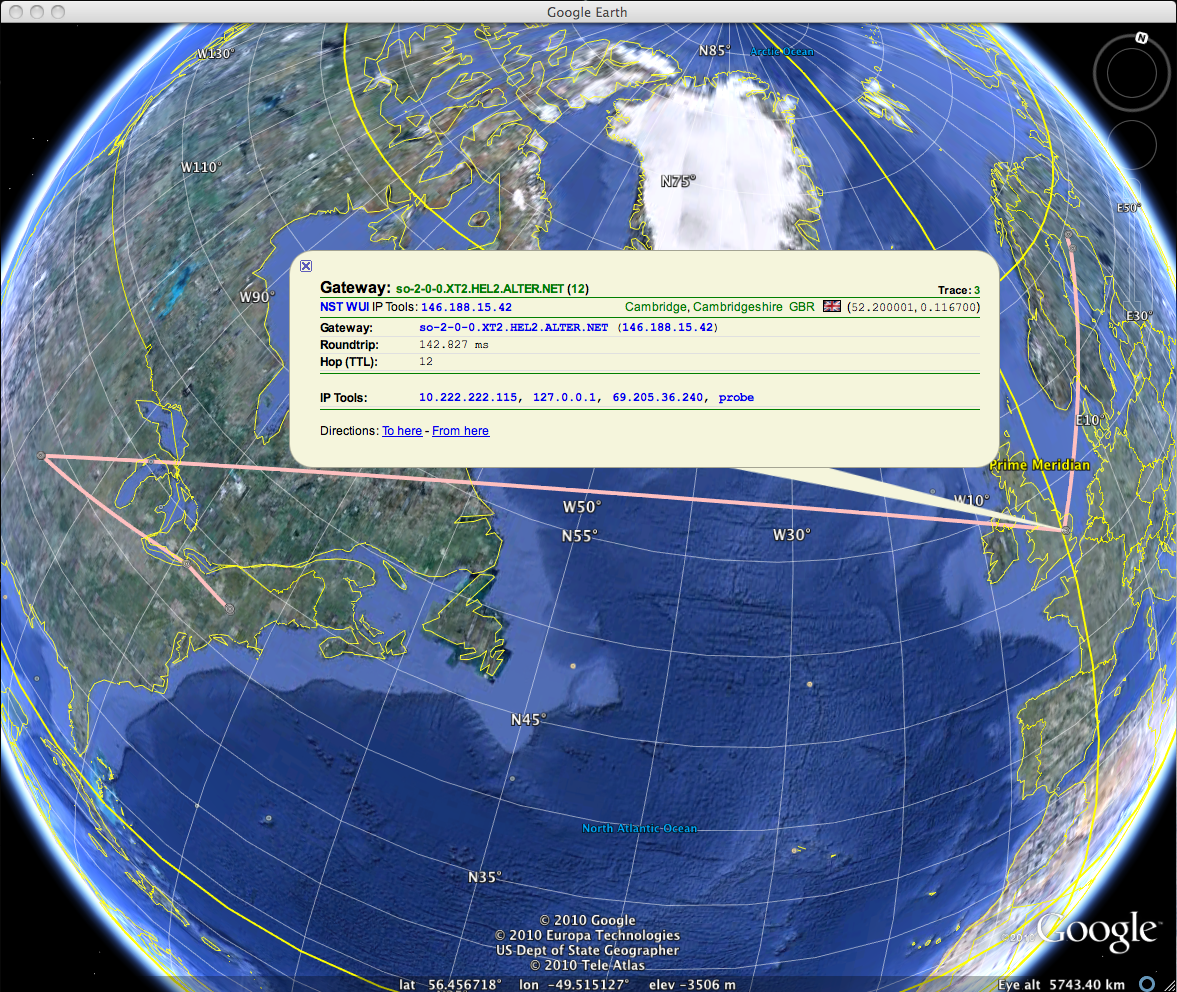
There is also a browser-based packet capture and protocol analysis system capable of monitoring up to four network interfaces using Wireshark, as well as a Snort-based intrusion detection system with a “collector” backend that stores incidents in a MySQL database. For web developers, there is also a JavaScript console with a built-in object library with functions that aid the development of dynamic web pages.
A great guide on what is available on the live distro and how to use each tools it’s present of the official wiki
Conclusions
This live CD it’s really filled with security tools and utility, so it could be really useful to set up in few minutes a location where you can do a security audit of a network or some hosts. It’s also really interesting the option to put it on a virtual machine, on the wiki there is a good how to on how to put NST on Virtualbox. So in few words: try and use it for your security audit, you’ll be satisfied for sure.
References: Wikipedia
Popular Posts:
- None Found

The documentation is excellent, too. Here’s a a good one.